Protecting your data is our greatest priority.
At Bluecopa, trust is at the heart of everything we do. Our infrastructure, processes, and products are all designed with the utmost care and attention to detail, so you can rest assured that your critical data is in safe hands.
We are committed to providing you with enterprise-level security and full compliance, so you can focus on what matters - growing your business and achieving your goals
We are committed to providing you with enterprise-level security and full compliance, so you can focus on what matters - growing your business and achieving your goals






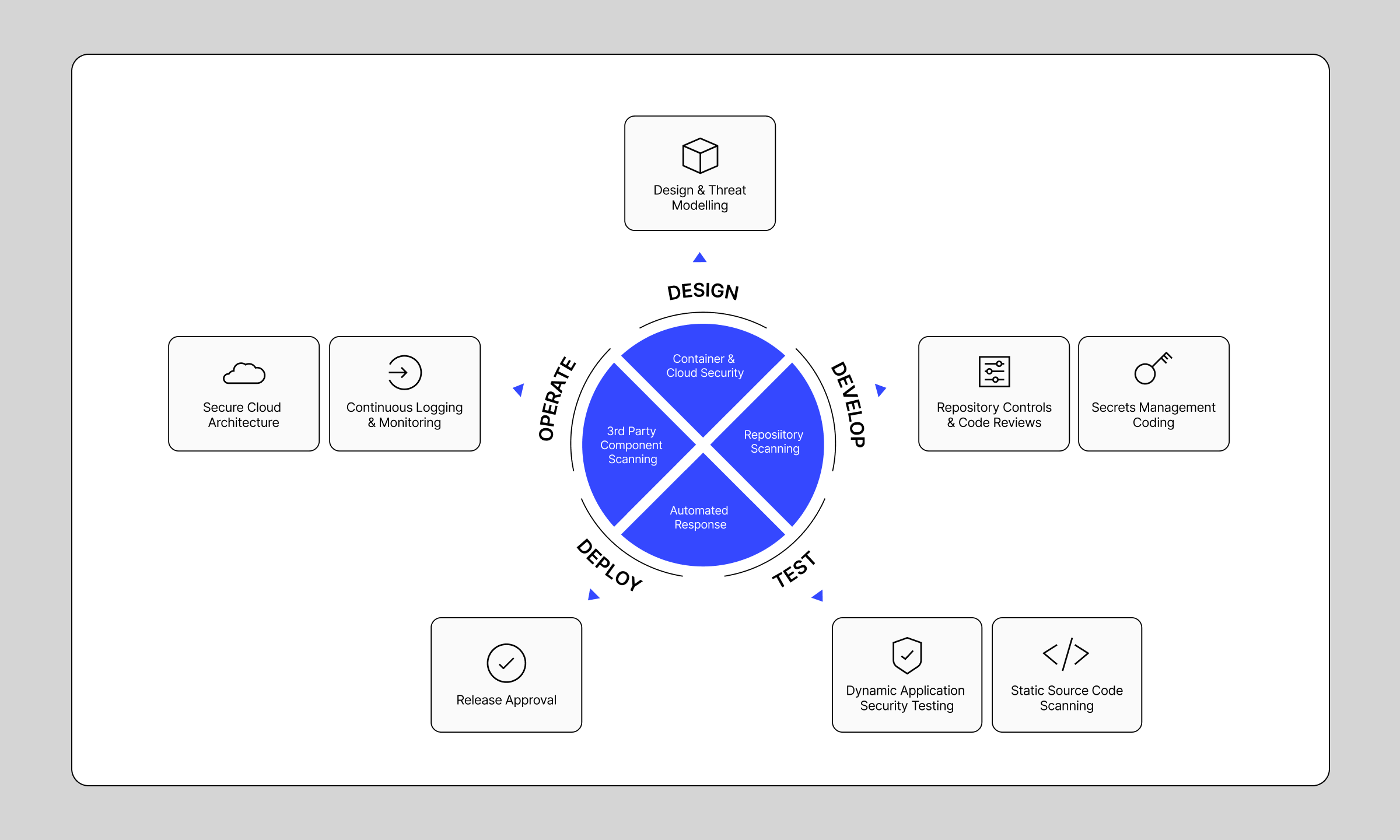
Shift Left Security
Bluecopa has a secure software development lifecycle (SDLC) that integrates security into all stages of the development process, from feature requests to production monitoring. We use tooling to trace a feature through the lifecycle and to automate security scanning and vulnerability tracking of systems, libraries, and code.
.png)
Advanced Security Features
We offer comprehensive security solutions to protect your data and workloads, including encryption, network controls, data governance, and auditing.
Platform architecture
To enhance security isolation and effectiveness, the Bluecopa platform architecture is divided into two distinct planes: the data plane and the control plane. The two-plane architecture simplifies permissions and reduces risk.
Data plane
The data plane is where your data is processed. You can find it either in your cloud service provider account or in, if you prefer, the Bluecopa account. The data plane includes Bluecopa runtime clusters and networking.
To ensure customer satisfaction, our data planes feature multiple workspaces that effectively separate staging and production environments for each customer. User access is gated to a particular workspace.
Control plane
The control plane is where your deployment is managed. It is located in the Bluecopa cloud service provider account. The control plane includes the web app, jobs, cluster management, SSO/authentication, and other features.
Seamlessly manage access rights
Role-based access control and comprehensive permissions ensure that only authorized users access data approved by the company administrator.
Secrets are Secret
We use AWS KMS (Key Management Service) at the control plane, which is the layer that manages the overall security of our system. On the data plane, which is the layer that stores and processes data, we use the cloud-specific key management system for each cloud platform. For example, we use KMS in AWS and Cloud Key Management in GCP.
Keep track of everything with audit logs
We support both application and system audit logs. A comprehensive audit logging tells you who logged in, when, for how long, and what they did. This helps track down security incidents and investigate them.
Make the most out of data backups
Easily configure redundant data backups and store them in durable cloud storage, such as Amazon S3 or Google Cloud Storage.
Encryption is built-in
Data in transit is encrypted using TLS 1.3. All data at rest in the data plane cluster is stored in encrypted volumes specific to the cloud provider. Additionally, all databases and storage in the control plane are encrypted.
For example, in AWS, we use S3-SSE-S3 and AWS EFS-FIPS 140-2. All data stored by Google Cloud is encrypted at the storage layer using the Advanced Encryption Standard (AES) algorithm, AES-256. Google Cloud uses Tink, which includes a FIPS 140-2 validated encryption module, to implement encryption consistently across its cloud platform.
For example, in AWS, we use S3-SSE-S3 and AWS EFS-FIPS 140-2. All data stored by Google Cloud is encrypted at the storage layer using the Advanced Encryption Standard (AES) algorithm, AES-256. Google Cloud uses Tink, which includes a FIPS 140-2 validated encryption module, to implement encryption consistently across its cloud platform.
Compliance
Certified with SOC 2 Type I, Type II, and ISO, your data is secure in our cloud. Compliant with GDPR and CCPA regulations, Bluecopa meets the needs of highly regulated industries. You could contact your Bluecopa account team for SOC 2 Type I and Type II and ISO reports.


SOC 2 Type II sets the standard security controls among cloud service providers. It furnishes in-depth detail regarding security controls implemented within an organization.
Moreover, it encompasses the validation checks performed by auditors to ensure the enduring presence of these controls throughout the audited timeframe.
Moreover, it encompasses the validation checks performed by auditors to ensure the enduring presence of these controls throughout the audited timeframe.

GDPR represents the EU General Data Protection Regulation, outlining safeguards for personal data originating from the European Union (EU) or European Economic Area (EEA).
Bluecopa adheres to GDPR standards as an organization, with the observability platform primed for GDPR compliance.
Bluecopa adheres to GDPR standards as an organization, with the observability platform primed for GDPR compliance.

The California Consumer Privacy Act ("CCPA") is a Californian privacy statute designed to shield consumers from businesses that mishandle their personal information, altering how businesses handle and safeguard consumer data they amass and retain.
Bluecopa aligns with CCPA mandates as an organization, and the Bluecopa platform is geared toward CCPA compliance.
Bluecopa aligns with CCPA mandates as an organization, and the Bluecopa platform is geared toward CCPA compliance.

Focused on the prerequisites of information security management system (ISMS), ISO/IEC 27001 sets the benchmark for policy and management controls in information security.
Bluecopa holds ISO 27001:2013 certification.
Bluecopa holds ISO 27001:2013 certification.
Trust and Privacy
Bluecopa is a trusted platform for businesses of all sizes. We build security into our products and services from the ground up. We follow rigorous operational security practices to protect our customers' data.
Vulnerability management
Bluecopa has automated its vulnerability management process and uses multiple security tools to scan our internal systems and associated third-party/open-source packages for vulnerabilities daily.
We also perform static and dynamic code analyses (SAST and DAST) before deploying new code or images. Additionally, we engage external experts to evaluate our public-facing sites to identify potential risks.
We monitor open vulnerability platforms, such as CVE Trends and Open CVDB, to stay up-to-date on the latest vulnerabilities. We have established robust response processes, quickly assessing the impact of any vulnerabilities reported. This enables us to replicate reported vulnerabilities and resolve zero-day threats rapidly.
Our vulnerability management program is subjected to addressing severity-0 vulnerabilities, including zero-day, with utmost urgency. We prioritize the resolution of these vulnerabilities over other deployments.
We also perform static and dynamic code analyses (SAST and DAST) before deploying new code or images. Additionally, we engage external experts to evaluate our public-facing sites to identify potential risks.
We monitor open vulnerability platforms, such as CVE Trends and Open CVDB, to stay up-to-date on the latest vulnerabilities. We have established robust response processes, quickly assessing the impact of any vulnerabilities reported. This enables us to replicate reported vulnerabilities and resolve zero-day threats rapidly.
Our vulnerability management program is subjected to addressing severity-0 vulnerabilities, including zero-day, with utmost urgency. We prioritize the resolution of these vulnerabilities over other deployments.
Training on security-related practices
All employees receive security awareness training. Developers and designers also receive additional training on secure design and coding practices, which are more specific to their roles. This training helps them to create more secure applications that are less vulnerable to attack.
To ensure customer satisfaction, our data planes feature multiple workspaces that effectively separate staging and production environments for each customer. User access is gated to a particular workspace.
Automated continuous compliance
All compliance controls are monitored using an integrated compliance and security tool. This tool integrates with all of Bluecopa's infrastructure, development, and production systems, helping you monitor compliance controls live.
Continuous security assessments
A consultant pentester or security expert trained in ethical hacking is deployed to test Bluecopa's applications periodically. Also, cloud service providers conduct periodic tests and share the results with Bluecopa.
Bluecopa internal theft prevention
Bluecopa implements and monitors data loss prevention (DLP) techniques to prevent data theft from insiders. Access to systems and data is granted only to authorized personnel on a need-to-know basis.
Secure software development lifecycle
Bluecopa has a secure software development lifecycle (SDLC) that integrates security into all stages of the development process, from feature requests to production monitoring. We use tooling to trace a feature through the lifecycle and to automate security scanning and vulnerability tracking of systems, libraries, and code.
Privacy
Bluecopa is committed to protecting your privacy. We understand that the data you analyze using Bluecopa is pivotal to you and your customers, and we may be subject to various privacy laws and regulations.
If you want to gain a better understanding of how Bluecopa fits into these regulatory frameworks, we encourage you to get in touch with us.
If you want to gain a better understanding of how Bluecopa fits into these regulatory frameworks, we encourage you to get in touch with us.

Future-proof your finance operations, today
Automate complex finance processes and systems. Accelerate decisions with Bluecopa's Al-powered, real-time insights.
Book a demo